SIP port on Checkpoint firewalls
So here is another issue I have come across twice this week alone.
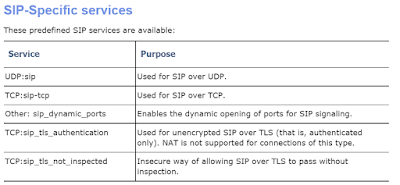
When setting up the TCP 5061 rules on firewalls between DMZ Internal and LAN on Checkpoint Firewalls, the default SIP rule being chosen by admins is SIP_TLS_AUTHENTICATION. However while a simple telnet will work between the servers (it may take 7-8 seconds extra) and it will look like it works but no logs in the Logger or errors about certificates.
What I found is that if you change the rule to SIP_TLS_NOT_INSPECTED this resolved the issue. We could then see traffic coming completely through.
Here is some information from checkpoint directly:
Source: https://sc1.checkpoint.com/documents/R76/CP_R76_VoIP_WebAdmin/87769.htm
When setting up the TCP 5061 rules on firewalls between DMZ Internal and LAN on Checkpoint Firewalls, the default SIP rule being chosen by admins is SIP_TLS_AUTHENTICATION. However while a simple telnet will work between the servers (it may take 7-8 seconds extra) and it will look like it works but no logs in the Logger or errors about certificates.
What I found is that if you change the rule to SIP_TLS_NOT_INSPECTED this resolved the issue. We could then see traffic coming completely through.
Here is some information from checkpoint directly:
Source: https://sc1.checkpoint.com/documents/R76/CP_R76_VoIP_WebAdmin/87769.htm

Comments
Post a Comment