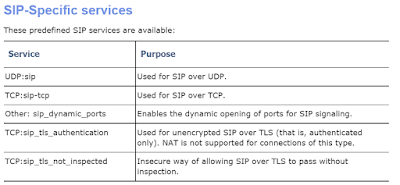
Outlook Certificate "Security Alert" issue with Exchange
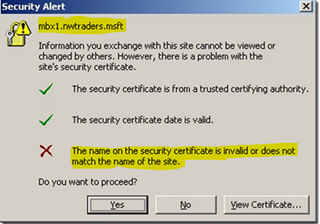
Another common issue with Exchange and Outlook is that end users see pop ups complaining about the name on the certificate not matching the cert itself. " The name on the security certificate is invalid or does not match the name on the site " Or " The security certificate has a valid name " is marked with a red X This tends to happen when the InternalURL does not match the certificate names. What this means in plain English is that the server name is either not on the certificate or does not match up. In many cases the servers will be built and use a single public wildcard certificate, however this wildcard certificate domain does not match the internal domain name. E.g. Mydomain.ie is the public SMTP name and wildcard cert *. mydomain.ie but the Active Directory domain is mydomain.local . We can "trick" the Exchange System into thinking that it is mydomain.ie and respond as such (No need to change domain n